Entra Private Access for Domain Controllers
- Maxime Hiez
- Entra ID
- 22 Aug, 2025
Introduction
Microsoft has announced the Public Preview of Microsoft Entra Private Access for Active Directory Domain Controllers, a major step forward in strengthening the security of hybrid environments. Integrated into the Security Service Edge (SSE) solution, this solution allows you to apply conditional access policies and multi-factor authentication (MFA) to internal resources authenticated via Kerberos, via the Global Secure Access platform.
What is Microsoft Entra Private Access ?
Private Access is a Zero Trust Network Access (ZTNA) solution managed by Microsoft that replaces or complements traditional VPNs to provide users with secure access to internal applications and resources (internal web applications, databases, RDP servers, domain controllers, etc.).
How it works and key benefits
Zero Trust security
An agent (Private Access sensor) is installed on the domain controller to intercept Kerberos requests and apply conditional access policies, even for legacy protocols that don’t support modern controls. This eliminates implicit trust within the network perimeter.
Uniformity of protections in a hybrid environment
This solution ensures a consistent security experience, whether the user is remote, on-premises, or in a hybrid environment. Application traffic remains local to maintain performance, while authentication requests are redirected to Entra for evaluation, ensuring consistent application of security policies.
Insider threat protection
By strengthening security at the domain controller level, this approach enables Identity Threat Detection and Response (ITDR) : every request is verified, lateral movements are blocked, and MFA can be required even on critical internal resources.
Granular Controls by Resource
Administrators can define highly specific policies at the Service Principal Name (SPN) level :
- Require MFA for file shares (CIFS)
- Allow access from compliant devices to MSSQL servers
- Enforce strong authentication for sensitive RDP servers
Simplified interface and administration
Configuration is done via the Microsoft Entra portal. From this interface, you can register domain controllers, configure application segments (SPNs), assign policies, and distribute them without restarting the agents.
Robust and flexible deployment
Features such as Audit Mode, SPN exclusion, unmanaged device blocking, and Break Glass mode (emergency bypass) enable gradual and secure scaling without service interruption.
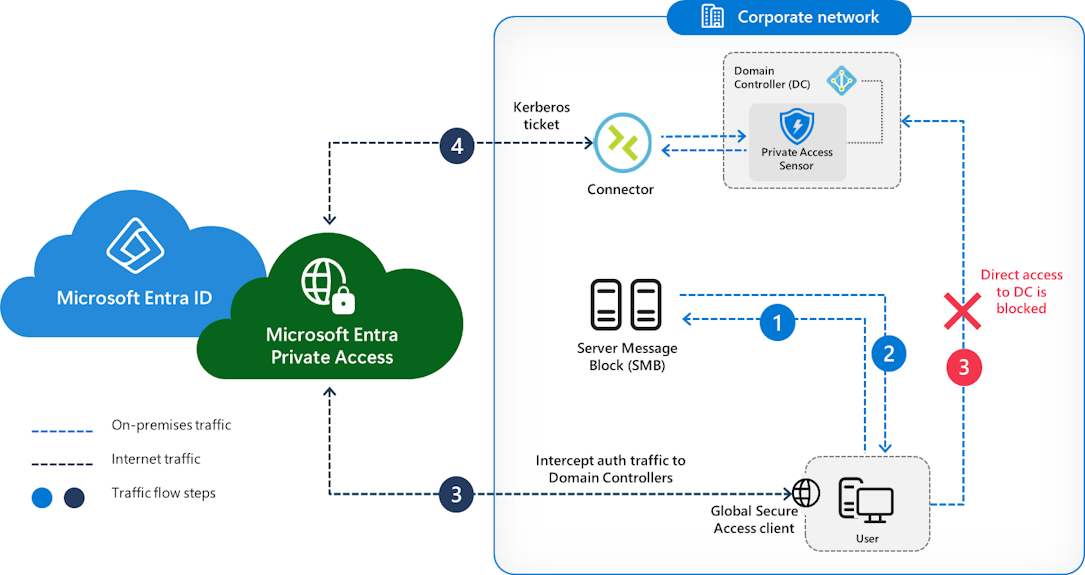
Why this announcement is important ?
- Blocking lateral movement : Interception at the heart of the domain controller, one of the most critical vectors of compromise.
- Seamless deployment : No need to rewire the network or install new on-premises appliances.
- Better visibility and control : Centralized policy, dynamic distribution, phased deployments.
- Suitable for mixed environments : Perfect for infrastructures combining on-premises and hybrid cloud, without compromising on performance or security.
Recommended action plan for administrators
- Install the Private Access Sensor agent on a pilot domain controller
- Enable Audit Mode to measure the impact before going live
- Define SPN policies gradually, starting with critical resources
- Use SPN exclusions as needed for a phased rollout
- Configure MFA and conditional access policies
- Prepare Break Glass scenarios in case emergency access is needed
- Monitor via logs, detect anomalies, and block risky access
Conclusion
The Public Preview of Microsoft Entra Private Access for Active Directory Domain Controllers represents a significant step forward in hybrid security. By bringing Zero Trust principles directly to domain controllers, without redesigning the infrastructure, Microsoft enables robust, flexible, and consistent protection across legacy protocols and cloud environments.
Sources
Did you enjoy this post ? If you have any questions, comments or suggestions, please feel free to send me a message from the contact form.
Don’t forget to follow us and share this post.