How to activate Defender EDR in "Block Mode"
- Maxime Hiez
- Defender , Tutorial
- 12 Nov, 2025
Introduction
In a context of constantly evolving cyber threats, antivirus solutions are no longer sufficient to effectively protect workstations. Microsoft Defender for Endpoint’s Block Mode is an often overlooked but essential feature for strengthening endpoint protection in a Microsoft 365 environment. It allows EDR (Endpoint Detection and Response) to intervene even on devices using third-party antivirus software, actively blocking detected threats instead of simply reporting them. By enabling Block Mode, you empower Defender to act as an additional layer of protection, capable of stopping a malicious executable or post-exploitation activity as soon as it is identified.
Prerequisites
A Windows 10/11 PC
- A Windows 10/11 PC enrolled in Intune.
An Entra ID group
- An Entra ID security group that contains the relevant PCs.
Licences nécessaires
- Microsoft 365 Business Premium, Microsoft 365 E5.
- Microsoft Defender for Endpoint Plan 2 in addition to another license (E3, …).
Administrator roles
- An account with the Global Administrator or Intune Administrator role to access the Microsoft Intune Admin Center.
- An account with the Global Administrator or Security Administrator role to access the Microsoft Defender Portal.
Step 1 : Sign in to the Microsoft Defender Portal
Sign in to the Microsoft Defender Portal by opening your web browser to https://security.microsoft.com.
Step 2 : Activate Block Mode
In the left menu, click System, then Settings.
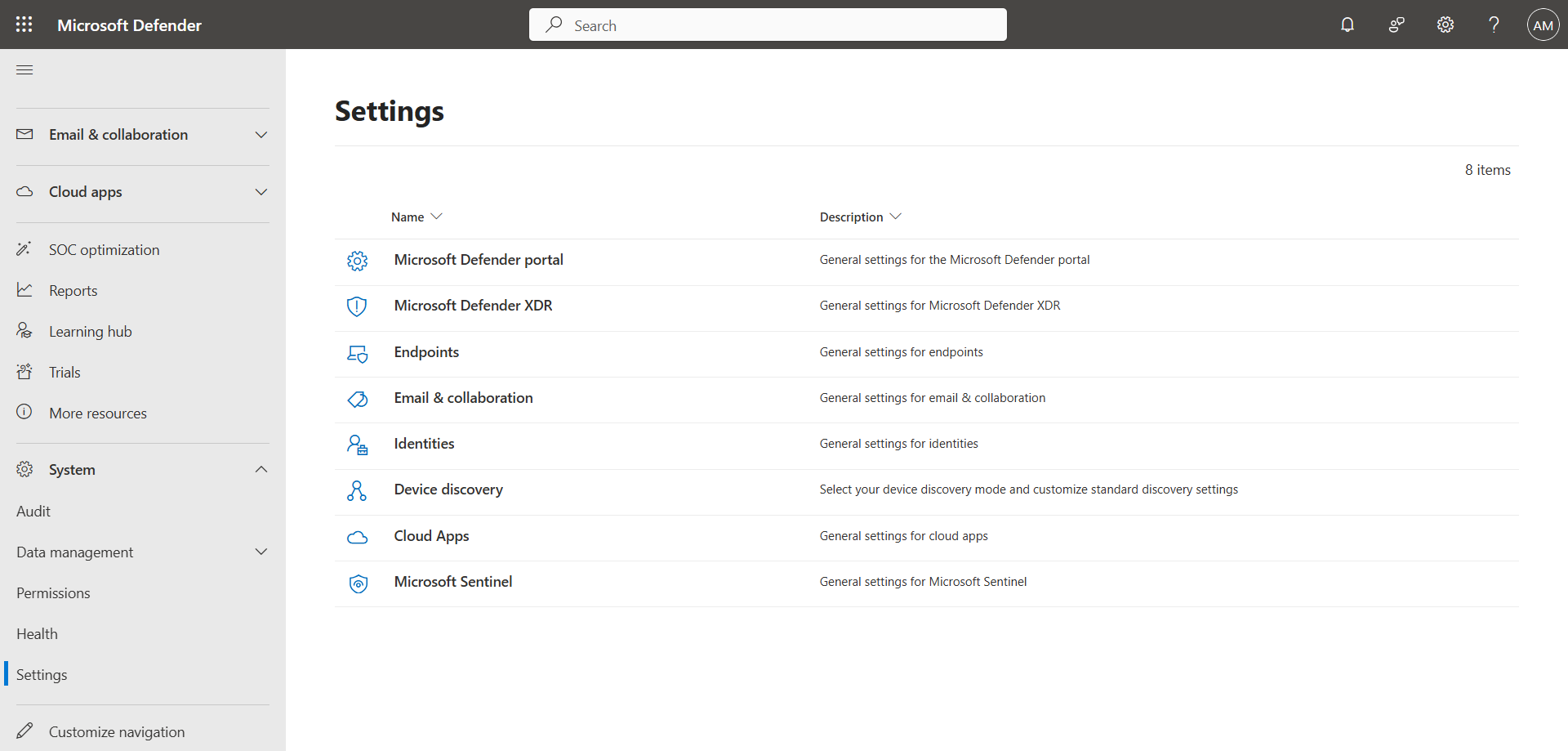
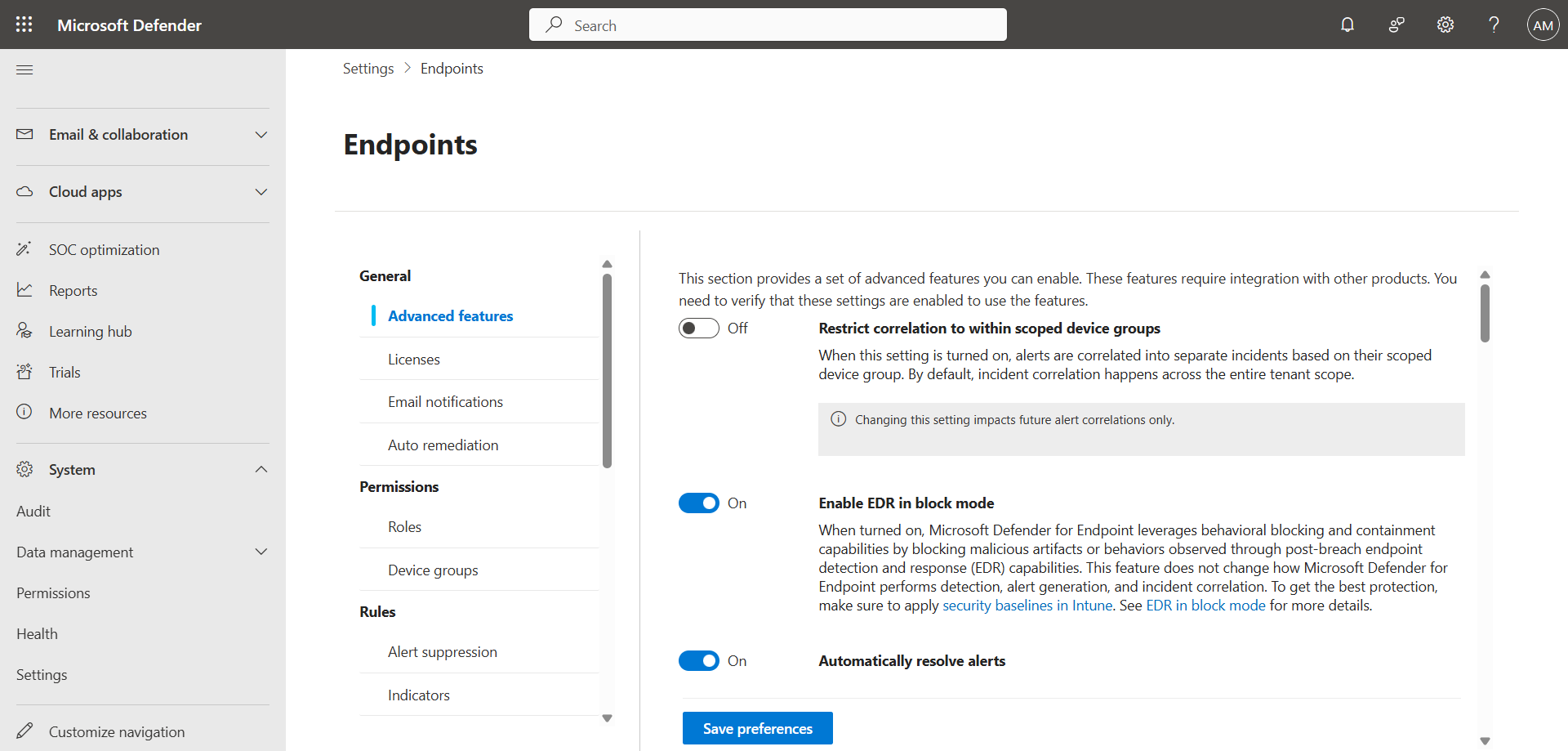
Click Endpoints, then Advanced features, and activate the Enable EDR in block mode switch.
Step 3 : Sign in to the Microsoft Intune Admin Center
Sign in to the Microsoft Intune Admin Center by opening your web browser to https://intune.microsoft.com.
Step 4 : Activate the Endpoint Detection and Response policy
In the left menu, click Endpoint security, then Endpoint detection and response.
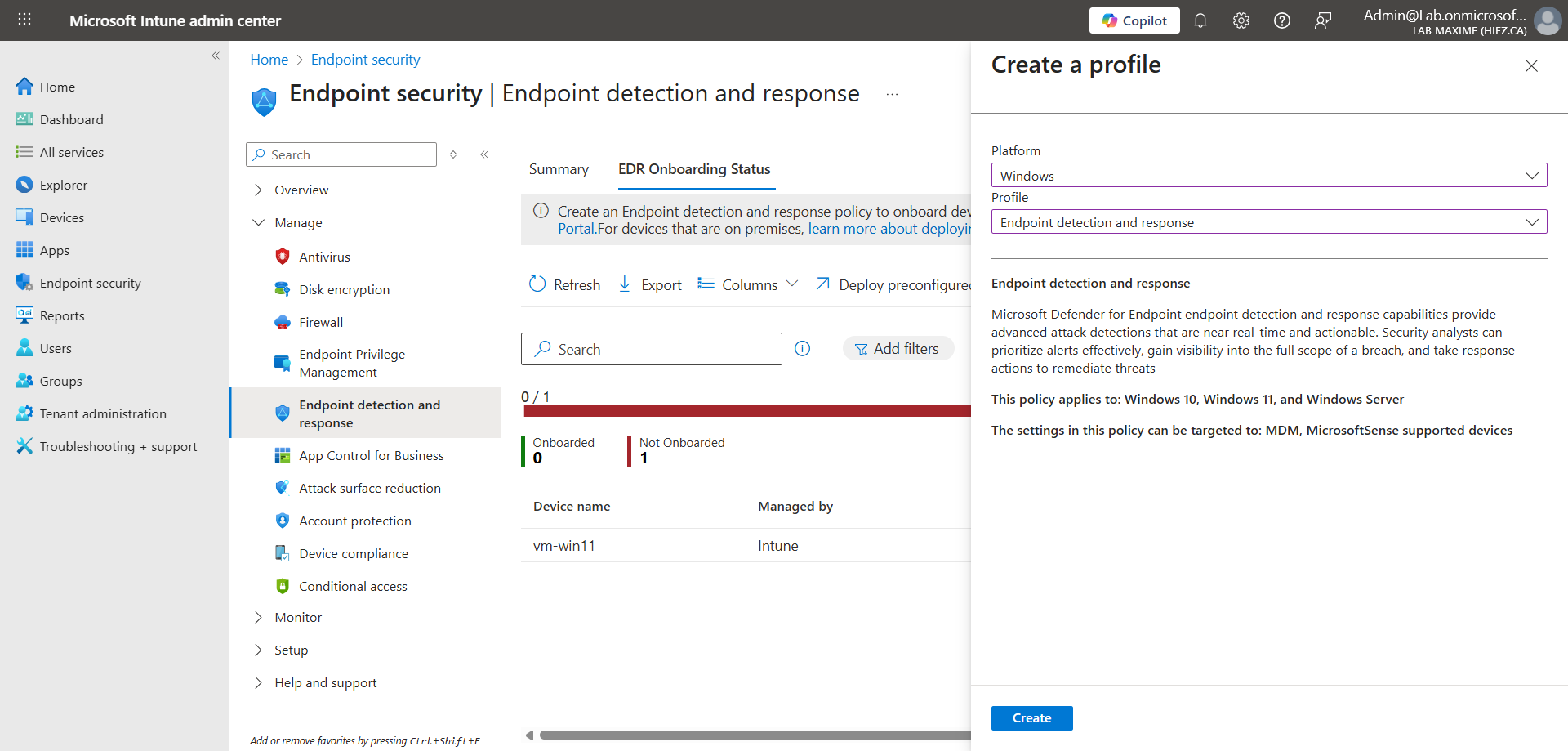
Click Deploy preconfigured policy, and create a policy for the Windows platform, keeping all the default options.
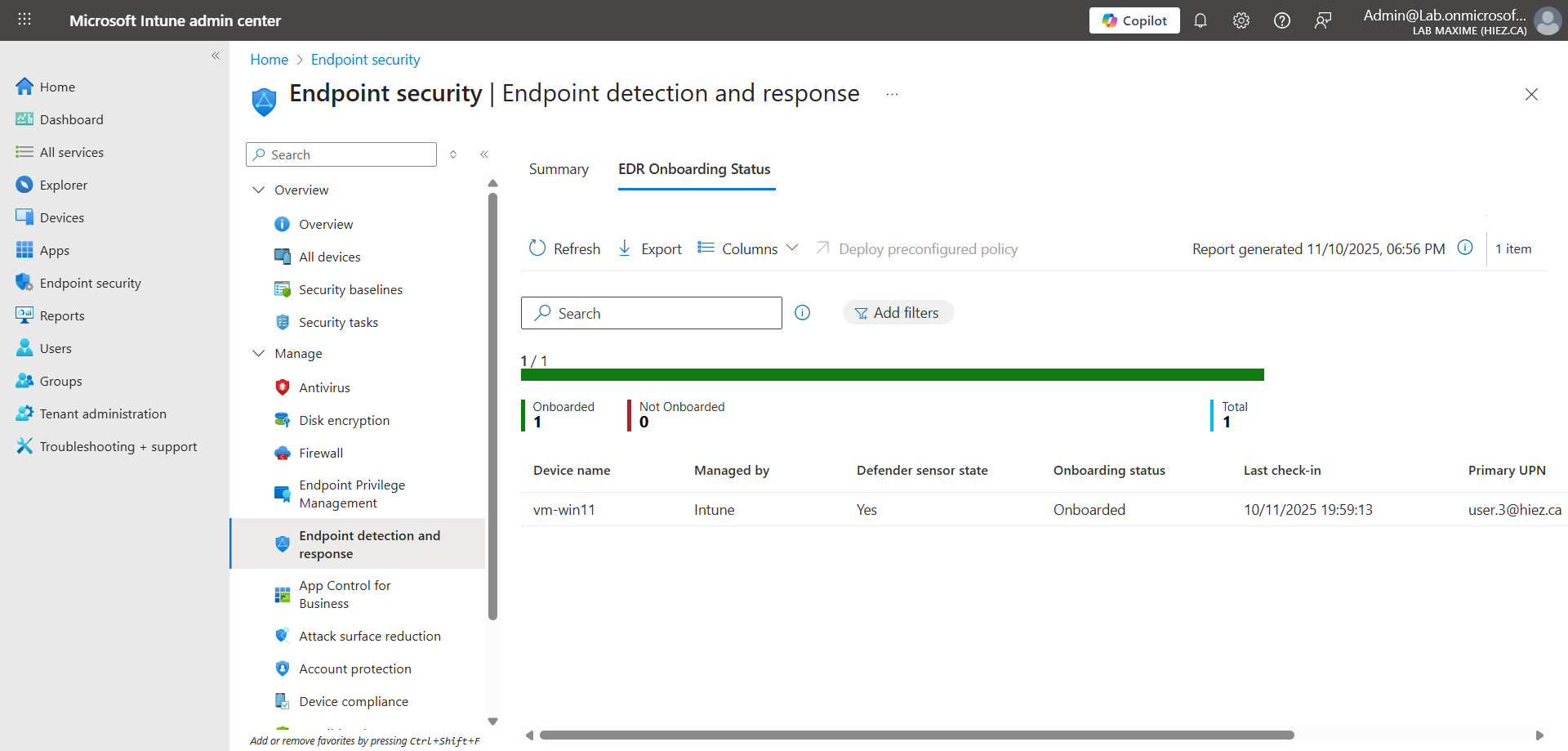
After a few minutes, the policy is deployed on the device.
Step 5 : Validate the Block Mode
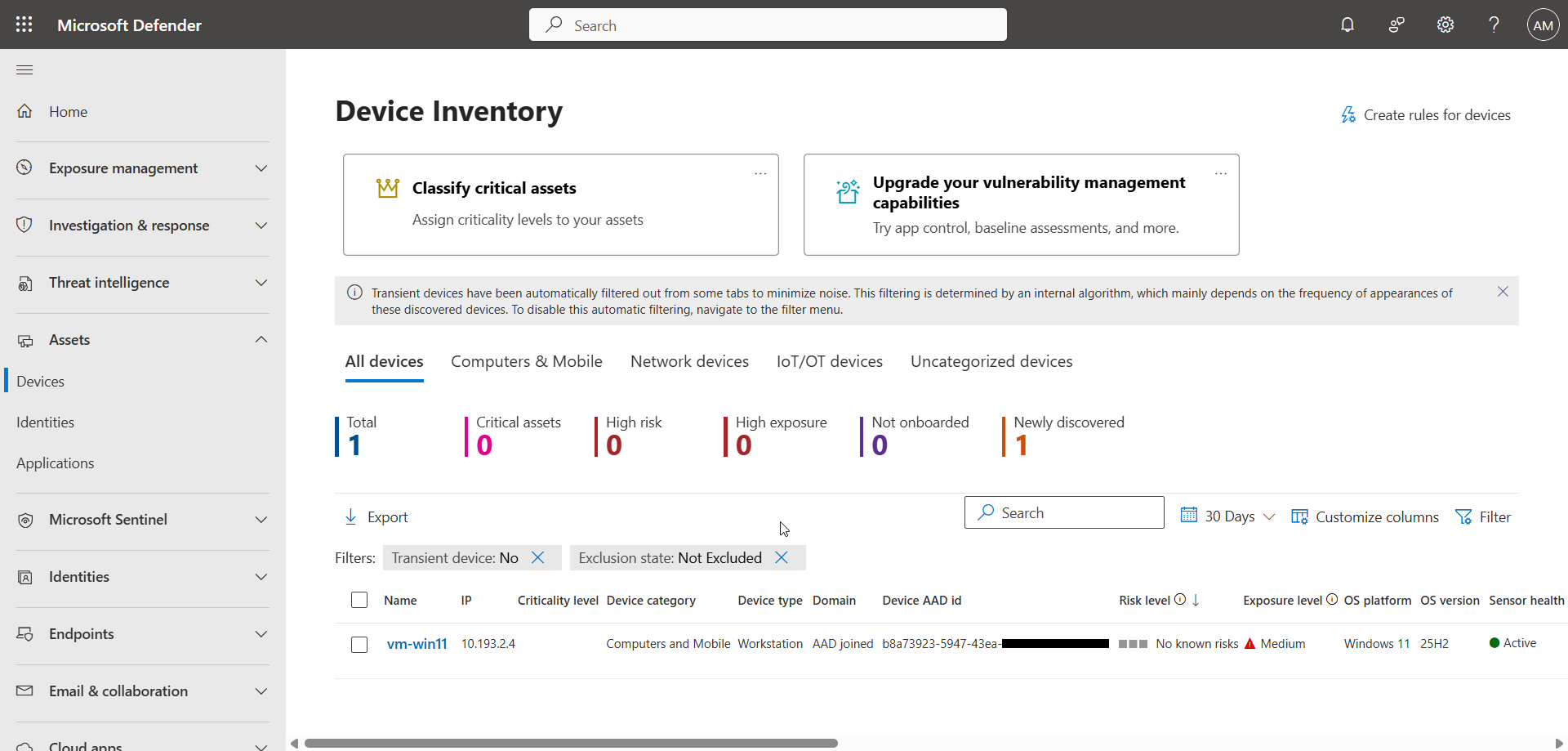
In the left menu, click Assets, then Devices.
The device is now visible in the Defender console.
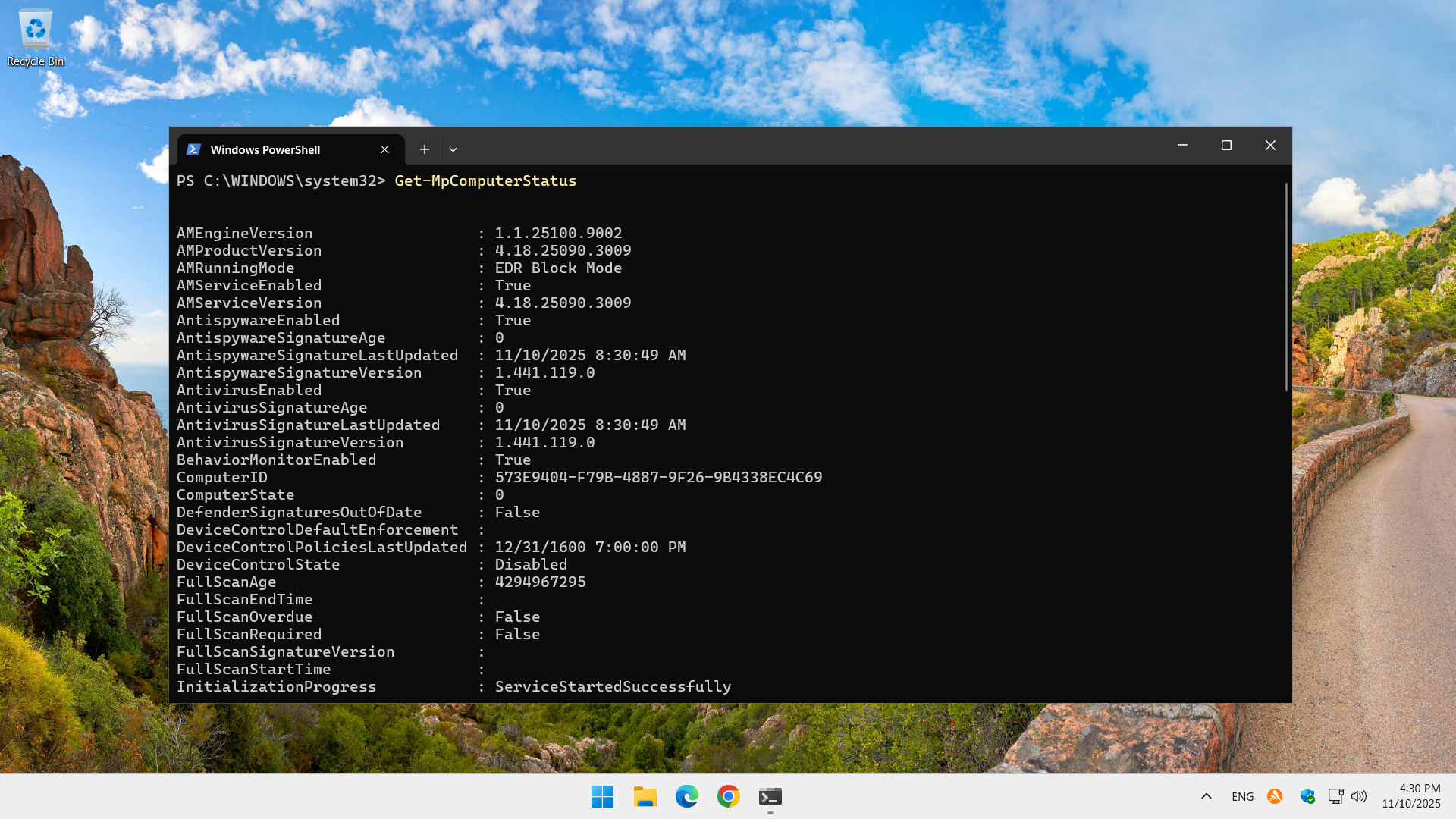
It is also possible to verify the successful deployment via the following PowerShell command :
Get-MpComputerStatus
As you can see on my computer, the AMRunningMode attribute returns the value EDR Block Mode. You can also see in my taskbar that I have two antivirus softwares, Avast and Defender.
Conclusion
You now know how to enable Defender EDR in Block Mode.
Sources
Microsoft Learn - Endpoint detection and response in Block Mode
Did you enjoy this post ? If you have any questions, comments or suggestions, please feel free to send me a message from the contact form.
Don’t forget to follow us and share this post.