
Protect against Next.js CVE-2025-29927 with Azure WAF
- Maxime Hiez
- Azure
- 28 Mar, 2025
Introduction
In March 2025, a critical vulnerability was identified in earlier versions of Next.js, known as CVE-2025-29927. This vulnerability allows permission checks within Next.js applications to be bypassed, potentially leading to unauthorized access and security compromise. Microsoft strongly recommends updating Next.js to the patched versions, but for applications that cannot be updated immediately, Azure Web Application Firewall (WAF) provides an effective mitigation solution.
CVE-2025-29927 vulnerability details
CVE-2025-29927 affects Next.js versions prior to 12.3.5, 13.5.9, 14.2.25, and 15.2.3. It allows attackers to bypass authorization checks by using specific requests with the x-middleware-subrequest header. Next.js versions 11.x do not currently have patches available, making mitigation via Azure WAF particularly important for these versions.
Recommended update
Microsoft recommends updating Next.js to one of the following versions to eliminate the vulnerability :
- Next.js 12.3.5
- Next.js 13.5.9
- Next.js 14.2.25
- Next.js 15.2.3
For 11.x versions and applications that cannot be updated immediately, creating a custom rule in Azure WAF can help mitigate this vulnerability.
Creating a custom rule in Azure WAF
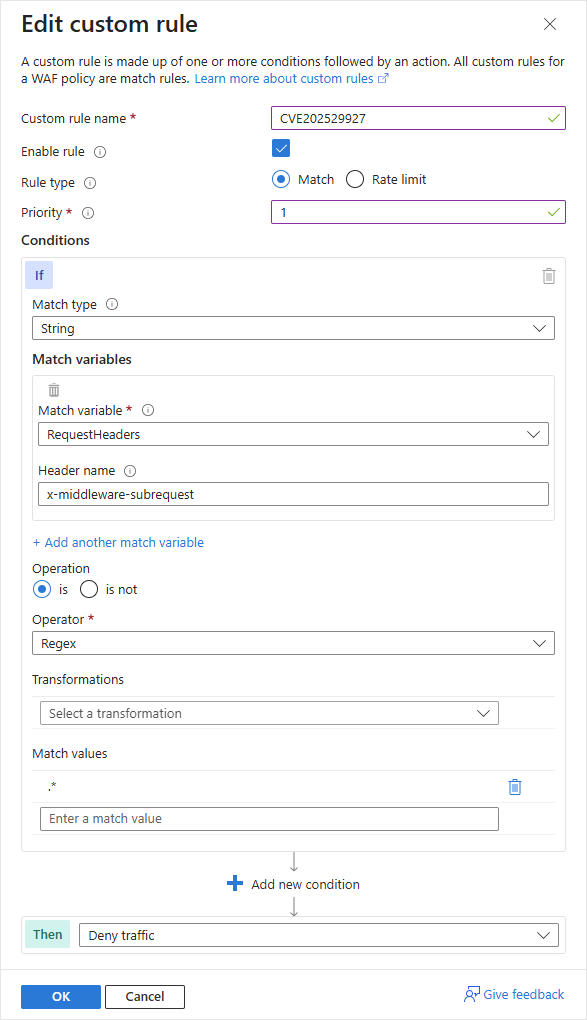
Here are the steps to follow to protect your application against CVE-2025-29927 :
- Log in to your Azure account and access your Web Application Firewall.
- Click Settings, then Custom Rules.
- Add a custom rule : Click Add Custom Rule, and give your rule a name (example CVE202529927) and a priority.
- Configure the conditions :
- Match type : String
- Match variable : RequestHeaders
- Header name : x-middleware-subrequest
- Operation : is
- Operator : Regex
- Match values : .*
- Action : Select Deny Traffic to block all requests containing this header.
- Save and apply the new rule.
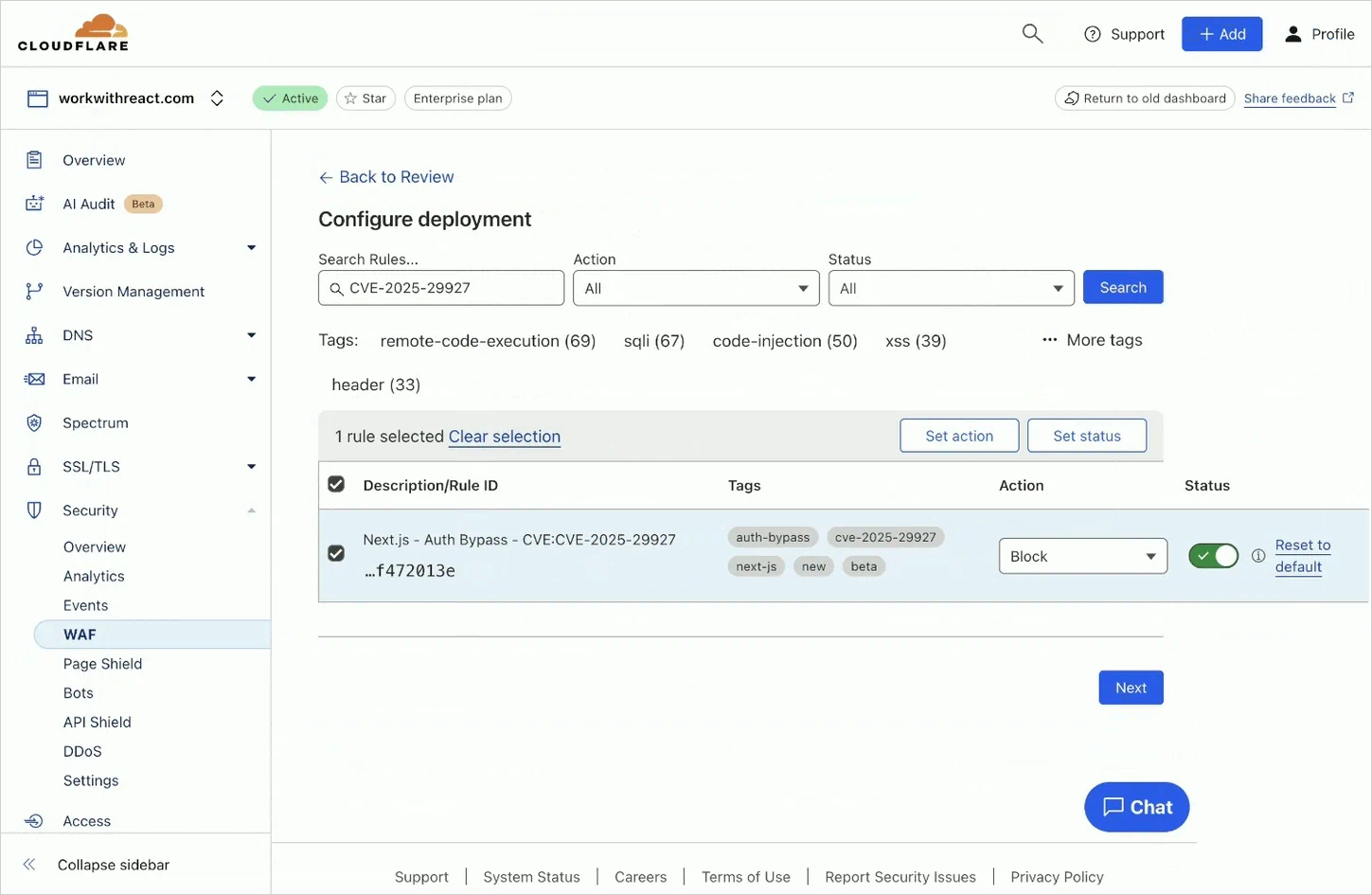
Solution via Cloudflare
For Cloudflare users, a managed WAF rule is available to protect against this vulnerability. This rule can be enabled in the Cloudflare dashboard :
- Go to the Cloudflare portal.
- Click Security, then WAF, and Managed rules.
- Search for the rule CVE-2025-29927 and enable the Status switch.
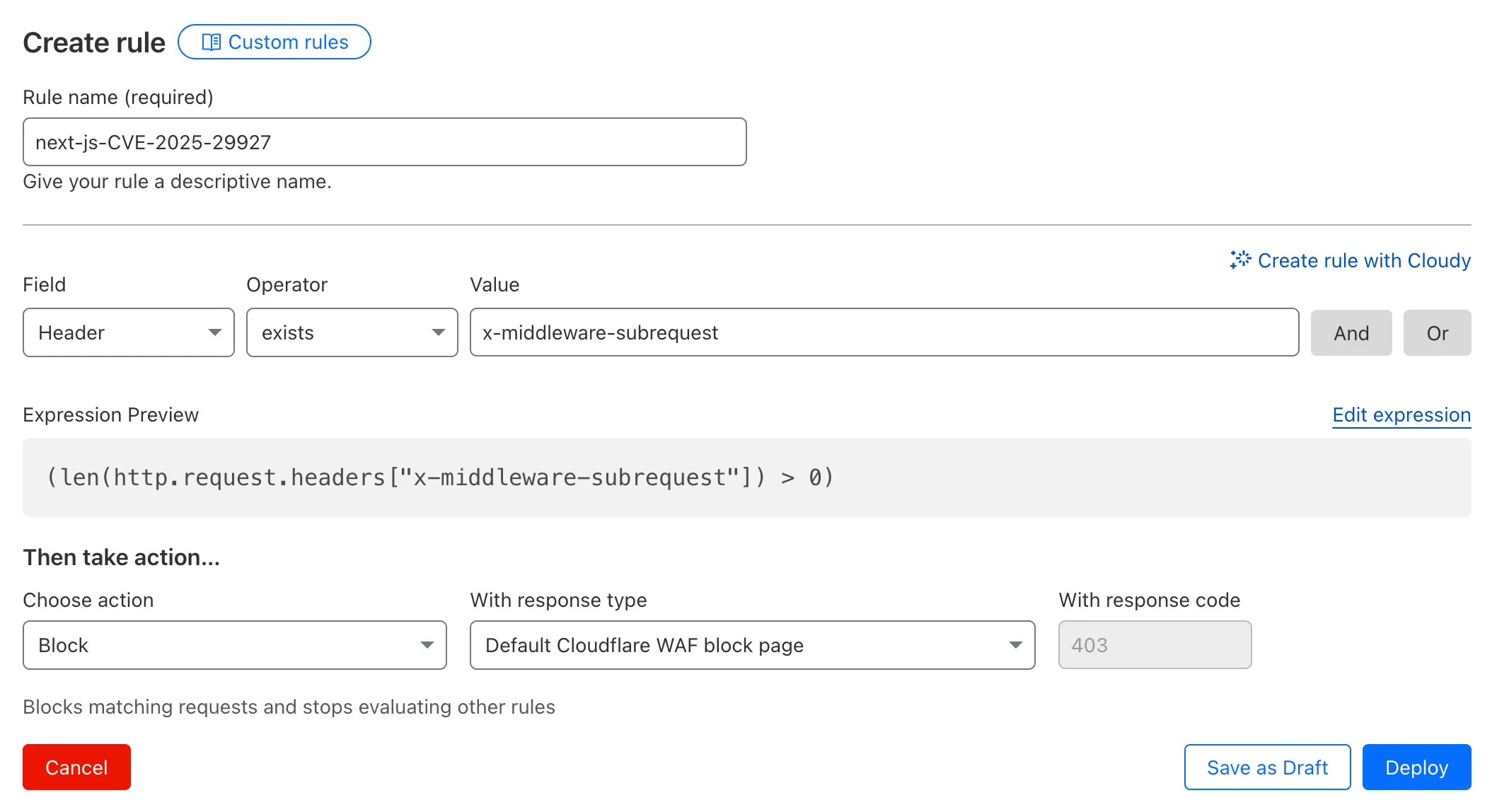
You can also create a manual rule with the following query :
(len(http.request.headers["x-middleware-subrequest"]) > 0)
Conclusion
The CVE-2025-29927 vulnerability in Next.js poses a serious security risk to web applications. By updating Next.js to patched versions or using Azure Web Application Firewall to create custom rules, organizations can protect their applications from this threat. It is crucial to remain vigilant and take proactive steps to secure your web environments.
Sources
National Vulnerability Database - CVE-2025-29927 details
Did you enjoy this post ? If you have any questions, comments or suggestions, please feel free to send me a message from the contact form.
Don’t forget to follow us and share this post.